Streamline Your Vulnerability Management with the
SAINT 8 Security Suite
Key features of SAINT 8 are highlighted below

 Enterprise Functionality
Enterprise Functionality
Multiple Scanner Deployments Deploy multiple SAINT 8 scanners to support large enterprise environments or distributed scanning. |
Faster Load Balanced Scans Balance the work among nodes in a network for faster scanning. |
Easy Scheduling Schedule scans to run across multiple scanner nodes in a single job. |
![]()
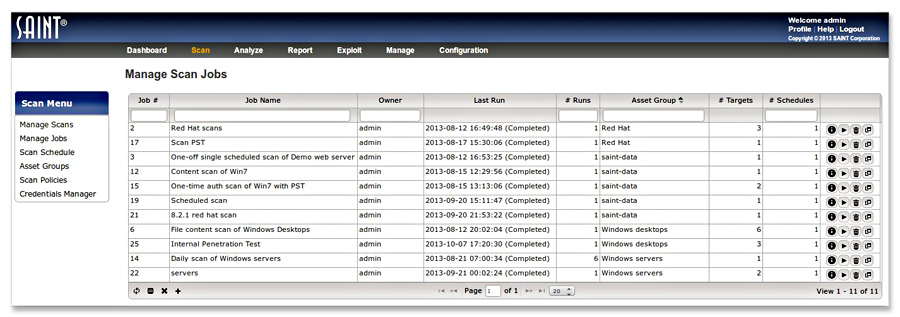
Friendly Integrated Interface
![]()
Integrated Tools Scan, exploit, report, view dashboards, and more, all from a single navigation bar. Navigate to other parts of the interface while a scan is running. |
Friendly Interface User interface based on function (compliance, vulnerability, etc.). Easy selection of scan targets with searches and sorts. |
Dynamic Control of Data Presentation Wide screen grid presentation allows fast queries, dynamic sorting, column selectors and multi-query filtering of data. |
![]()
 Intuitive and Direct Workflows
Intuitive and Direct Workflows
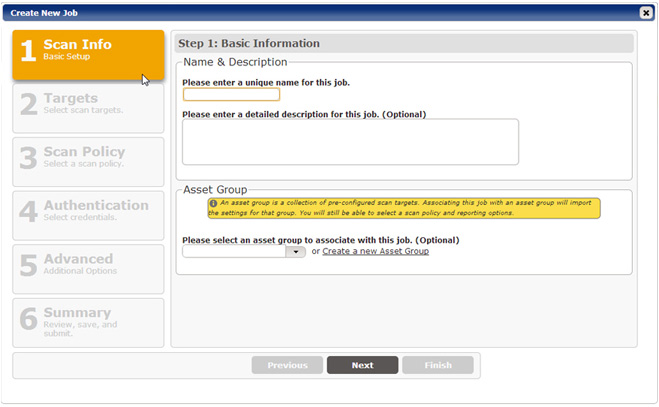
Easy Scan Set-Up Step-by-step wizard for creating a job; adding targets; setting target exclusions; setting and managing exclusions; configuring job-specific configurations, such as attack rules, timeout values, ports, email notification, etc.; scheduling immediate, scheduled or recurring scans. |
Intuitive Workflow Easy scanning workflow from discovery to target selection/exclusion, policy setup, customization and execution. |
Easy Reporting Step-by-step wizard for creating reports with over 150 configuration options. Merge the results from multiple scans into one report. |
Easy Scan Set-up with The SAINT 8 Wizard
* Optional Step
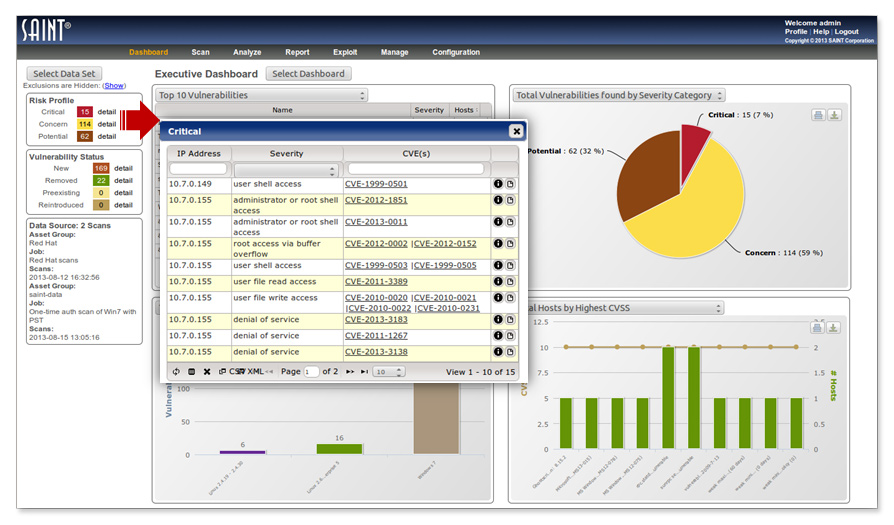
Data Drill Down and Analysis
Custom Dashboards with dynamic drill down to results
![]()
 Vulnerability, Exploit & Configuration Audit Integration
Vulnerability, Exploit & Configuration Audit Integration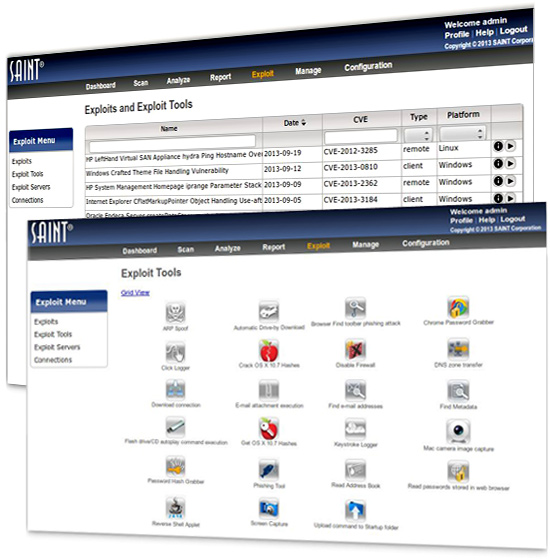
Because the scanner is integrated with configuration assessments and exploit software, SAINT 8 gives you a holistic picture of your risk profile to help prioritize your remediation to the most critical exploitable vulnerabilities. |
Centralized setup, execution, and control of –
|
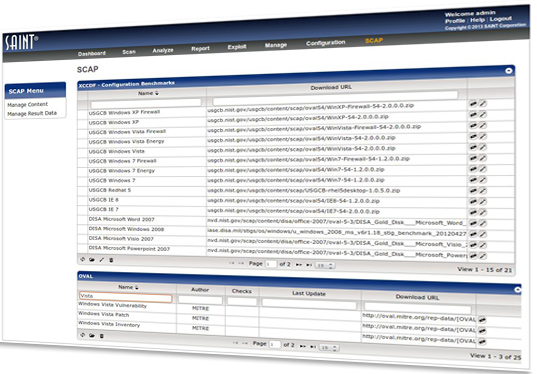
 Dedicated SCAP Module
Dedicated SCAP Module
SCAP scanning, analysis, and compliance reporting. Policy editor to create custom policies based on NIST benchmarks.
|
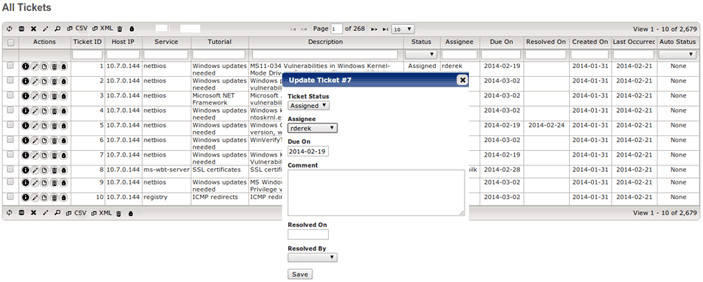
Remediation Ticketing
Generate Workflow Tickets Based on ticket policies and rules you define. |
Easy Ticket Updates and Searches Bulk update features for routine tasks like work assignment, ticket status, setting due dates and resolution information. |
Keep History and Document Retain a history of actions taken over time and document critical information about actions taken. |
![]()
Risk Management
In the past, customers relied on severity levels such as High, Medium, or Low to prioritize their battle against vulnerabilities. However, security experts and asset managers today require more advanced and flexible methods for correlating risks to their infrastructure and critical business functions, and devising mitigation strategies. Whether it is associating vulnerabilities with industry-specific severity codes like PCI’s Severity codes, standards compliance based on Pass/Fail, prioritizing risk based on numeric scores like CVSS, or basing priorities on whether a vulnerability is exploitable, the ultimate decision is up to you. The value proposition from SAINT is to offer this flexibility and deliver easy-to-use solutions that facilitate the management of risk—not dictate how it should be conducted. |
SAINT Scanner Sample Mapping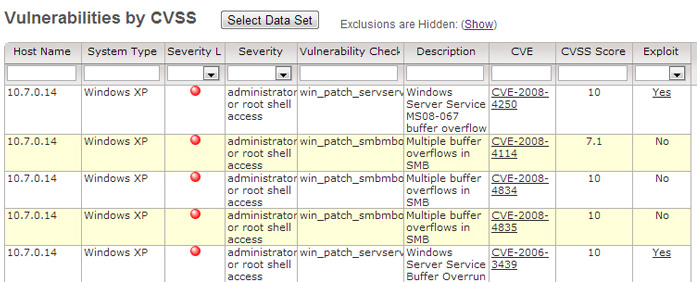 |
|
![]()
Interoperability with 3rd Party Investments
While vulnerability management is a key component of any complete risk management strategy, security solutions must be capable of interoperability across the holistic security landscape. SAINT solutions provide feature-rich functionality to collect and analyze results within SAINT or within other security investments, such as advanced analytics platforms and GRC tools. Direct interoperability with other SAINT partner solutions includes the following:
|
![]()
And Lots More ...
|
Custom Dashboards
|
|
Amazing Analytics
|
|
Policy Customization
|
|
Asset Management & Access Controls
|
|
API for Integration Support
|
|
Scalability
|